Security
Forgot Screen Time Passcode? Here’s How to Reset or Recover It
Its Screen Time feature on iOS devices tracks app usage, and apps shut down once the time expires, which is a great way...
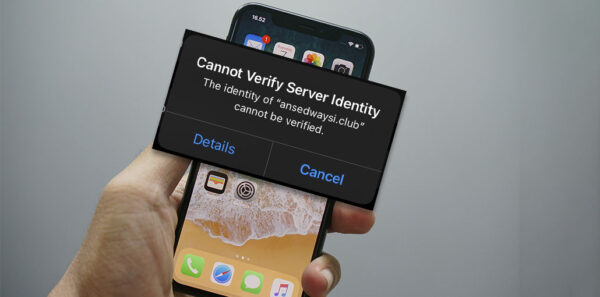
ByIsla GenesisOctober 31, 2025How to Fix the Cannot Verify Server Identity Error on Your iPhone
With the Mail app, you can access and handle every email you receive on your smartphone after an easy and fast setup process....
ByBarrett SOctober 29, 2025Top 10 Cloud Security Tools to Protect Business Data
Finding the best cloud security tools can greatly simplify threat detection and enhance compliance, whether protecting sensitive information, protecting a multi-cloud environment, or...
ByBarrett SOctober 12, 2025Are Cracked VPNs Safe? The Truth You Need to Know in 2025
A cracked VPN could promise access to essential security and privacy features for free. However, the risks aren’t worth the risk. Find out...
ByBarrett SOctober 3, 2025Discord Unblocked: 6 Ways to Access Discord Anywhere
My husband is a fervent player, and Discord is his primary source of communication when he’s looking to meet with friends for a...
ByZoey RileySeptember 27, 2025FastPeopleSearch Opt-Out Guide 2025: Protect Your Online Privacy
Have you ever felt anxious about your privacy online? If it’s helpful to you, then you’re not the only one. There are many...
ByAiden NathanSeptember 25, 2025Screen Time Passcode Guide: How to Set Up or Reset It
It is impossible to undervalue the significance of applications that screen time, especially when it comes to parent-child monitoring. Utilizing the Screen Time...
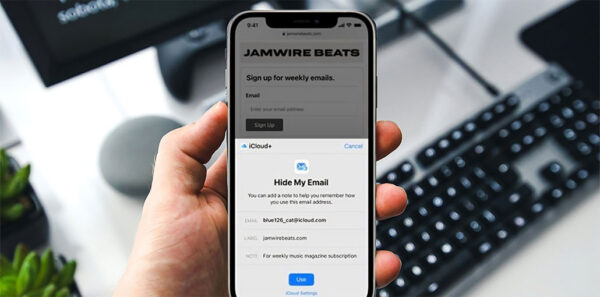
ByAiden NathanSeptember 24, 2025How to Use Apple Hide My Email to Protect Your Inbox
Sharing your personal email addresses could put your personal information at risk of data leaks and sharing. Fortunately, Apple allows you to keep...
ByBarrett SSeptember 22, 2025Fidelis Security’s Deception Technology: The Next Big Trend in Cybersecurity
Most cybersecurity vendors make broad claims about innovation. However, deception technology offers a distinct approach; one that can operate as intended in real-world...
ByAiden NathanSeptember 19, 2025Why Am I Not Receiving Emails? Troubleshooting Guide for 2025
Not receiving Gmail emails could have serious repercussions if they’re used for work or school. however. Luckily, finding solutions to this problem should...
ByBarrett SSeptember 17, 2025